How to Secure Your Website
Back in 2012, cybersecurity experts from Sophos Labs estimated that, on average, more than 30,000 sites are compromised every day. As some of you have calculated already, this equates to 900,000 hacked websites every month.
Of course, this was a long time ago, when the internet was much smaller. We don’t have any more recent statistics, but chances are, the current figures are much scarier.
There’s another problem – cybercriminals have evolved quite a bit over the years, and their attacks are now much more sophisticated than they used to be.
All this leads to one thing – securing a website is trickier than it used to be, and there’s no indication that it will ever get easier.
Let’s examine the problem more closely and see how you can deal with the security risks.
Why is Website Security Important?
Even if you run your project as a pastime hobby, you must recognize the serious repercussions of failing to manage it responsibly. For one, you have to think about your personal security. When hackers decide to target a particular website, often, one of their first steps is to find out who owns it. If you don’t take the necessary precautions, cybercriminals will go after your personal data and use it to perform identity theft.
You also have to protect your users. Few people actually think about it, but by signing up for and using your website, they effectively entrust their data to you. You’re responsible for keeping it safe, and you must take every precaution imaginable to protect it from the innumerable online threats we see daily.
Last but not least, you should consider the risk for the rest of the World Wide Web. If they manage to compromise your website, hackers can use it to host phishing pages or malware. If they break into your hosting account, they can employ it to launch global attacks on critical infrastructure.
In short, there’s no shortage of things cybercriminals can do if they decide that compromising your website is worth it. And what would the damage to your online business be?
It could be pretty serious.
Financial losses
Let’s start with the cyberattack-related outages. You can’t make money from your site if it’s down, and the bigger the project, the more significant the losses.
Furthermore, if a user lands on your site and sees that it’s not operational, they are unlikely to return and try again. The effects could be more long-lasting than they seem at first, especially if you are the target of multiple attacks.
Reputational harm
Let’s start with the cyberattack-related outages. You can’t make money from your site if it’s down, and the bigger the project, the more significant the losses. Furthermore, if a user lands on your site and sees that it’s not operational, they are unlikely to return and try again. The effects could be more long-lasting than they seem at first, especially if you are the target of multiple cyber attacks.
Reputational harm
Users aren’t particularly inclined to interact with organizations that don’t do enough to protect their data. The matter can even be escalated to court if they can prove that security hasn’t been your top priority. This could be particularly damaging to a small business.
Search engine rankings drop
Google doesn’t want to lead users to malicious sites, so if it detects something suspicious on your project, it will display a full-screen warning telling site visitors that something harmful may be up ahead. The service is called Google Safe Browsing, and it’s used by the world’s top browsers. Upon seeing a Google Safe Browsing alert, most visitors would click away, meaning lost profits and revenues. This isn’t the only issue.
In the past, a Google Safe Browsing alert would immediately drop you down the search results page. Nowadays, it’s no longer considered a ranking factor, but your SEO performance will likely suffer anyway because of the higher bounce rate. You’ll still need to claw back some lost ground, and if you have a history of security issues, you’ll likely have a hard time doing it.
If you’re serious about your project, you can’t take the threat lightly. However, to secure your site, you first need to know what you’re defending against.
How Do Websites Get Hacked?
The techniques hackers use to compromise websites are so many listing them all is not really practical. Instead, we can group the most popular attacks according to the part of the site they focus on and the damage they cause.
Let’s have a look at the details
Access control attacks
Your website and your hosting account are controlled via several interfaces, namely, the backend dashboard, the web hosting control panel, and the client area at your provider’s site. In addition, you may have FTP and SSH accounts to manage files, databases, and server software.
Every means for connecting to your hosting account is protected by its own set of login credentials, and if someone wants to attack you, getting their hands on those credentials will be high on their agenda. There are more than a few methods for exposing or stealing usernames and passwords.
Human error
If you’re not careful, an honest mistake could facilitate unauthorized access. For example, you bring a new person on board, meaning they need to access the site’s backend to do their job. However, instead of creating a new account and letting them use only the tools they need, you simply give them your admin username and password. You’ve already opened the opportunity for unauthorized access, and things could be much worse if you forget to reset the admin password once the employee is gone.
Brute-force attacks
During a brute-force attack, a hacker effectively guesses your username and password. Once again, cybercriminals use various techniques and exploit numerous mistakes to find the right combination.
They’ll start with simple combinations like “123456” or “qwerty.” Stats show that these are among the most common passwords out there, so the chances of multiple successful login attempts are pretty good.
If that doesn’t work, they’ll fire up the password-cracking tools and use them to make thousands of guesses until they have the correct credentials.
Modern password crackers are highly advanced and can guess even relatively strong passwords. However, hackers often don’t need to use them at all.
Users can’t remember dozens of different passwords for all their individual accounts, so they often reuse the same credentials across multiple services. These services sometimes get breached, exposing people’s login information.
Hackers can gain access to the leaked data, and because they know that people tend to use the same password on multiple accounts, they try them on numerous other login pages.
The attack is called credential stuffing, and it’s often extremely effective.
Social engineering
In a social engineering attack, the attackers impersonate someone you trust to gain information that grants access to your account. Phishing is the most common type of social engineering, and although it’s traditionally associated with emails, nowadays, hackers will use any vehicle you can imagine to run their scams.
Man-in-the-middle
When you interact with a website, information travels between your computer and the host server. It covers many miles and goes through quite a few servers, routers, and switches (collectively called hops) before reaching its destination. It contains quite a lot of sensitive data, including your login details.
If you don’t take the necessary precautions, it can be intercepted at many different points in its journey. In the wrong hands, the stolen data could do some serious damage.
Malware/keyloggers
Cybercriminals have it easy nowadays. There are dark web marketplaces where malware developers sell their products to wannabe crooks from all over the world. The competition is stiff, which has a twofold effect.
On the one hand, it keeps the price low, and on the other, it pushes creators to develop new features that make their products more versatile.
Because of all this, attackers can easily get their hands on a fairly sophisticated and cheap keylogger or password stealer. Sometimes, malware vendors even help with the distribution, and as a website owner, you present a pretty attractive target.
Vulnerabilities
Your website platform (e.g., WordPress) works on top of a web server (e.g., Apache), uses a database management system (e.g., MySQL), and is written in a specific programming language (e.g., PHP). Unfortunately, all these components have their bugs and vulnerabilities, and you won’t be surprised to learn that hackers are more than willing to take advantage of them.
They have scanners that analyze the server software and find the current version of all running applications and systems. When they determine which security patches have been applied, the attackers often use readily available exploits to take advantage of the active vulnerabilities.
Depending on the type of attack and vulnerability, the hackers can cause the following damage.
Remote code execution
Remote code execution does exactly what it says on the box. It’s a type of security vulnerability that allows hackers to execute arbitrary code on a remote machine. In the context of web hosting, it could mean taking complete control over the host server and using it for a variety of nefarious purposes.
File inclusion
In a file inclusion attack, hackers exploit a vulnerability that dynamically references malicious scripts. The goal is to execute the malware on the server or in the user’s browser. The malicious script may be located in a remote location, but it could also be hosted on the target account if the site fails to sanitize user-supplied content.
SQL injection
SQL injection vulnerabilities allow hackers to execute malicious queries straight from your site’s text fields. By inserting a carefully crafted string, they can use the web application’s access to the database to steal, modify, or delete data.
Cross-Site Scripting
Cross-Site Scripting (XSS) vulnerabilities allow hackers to inject a malicious script into a completely benign website. A successful XSS attack against your site enables them to send and execute malware on your visitors’ computers. Because the scripts are sent by a benign source (your site), their browsers run them without hesitation.
Denial of service
Denial of service attacks are considered less severe because they don’t harm website users or allow hackers to steal customers’ data. During them, cybercriminals use various techniques to cause one of the components and systems powering your website to fail. The result is either a significant slowdown or a full-on crash.
As you may know, the most popular attack of this kind is called Distributed Denial of Service (DDoS). During it, hackers use massive networks of infected devices (botnets) to send enormous waves of junk traffic to the target website. The goal is to overwhelm the victim server and bring the site down.
DDoS attacks are traditionally associated with hacktivism – cybercriminal activity that is supposed to raise awareness about a specific topic or act as a protest against the targeted institution. In other words, historically, DDoSing has rarely been financially motivated. In recent years, however, this has changed.
Hackers know that it’s up to them to decide when to stop bombarding the target with traffic, and they’ve lately started taking advantage of this. Nowadays, they contact the victim after bringing their site down, announcing that the attack won’t stop until a ransom is paid. In some cases, the downtime is so expensive yielding to the hackers’ demands actually makes sense.
Third-party services
Third-party services are integral to many websites, and cybercriminals are only too happy to exploit this. Although no provider is immune to attacks, digital advertising platforms get the most attention from hackers. In fact, abusing ads for malicious purposes is so popular there’s a term for it – malvertising.
Using various techniques, the hackers manage to compromise the advertiser and inject malicious code into some of the ads appearing on your website. They can redirect users to a dangerous URL or try to install malware. Because they use a script that everyone loads, they can indiscriminately attack your entire audience.
And since thousands of websites use the same advertising platform, the reach could be quite widespread.
Steps to Secure Your Website

A list of things you need to do to secure a website will never be complete. The threats are constantly evolving, and you need to stay on top of them all the time. Nevertheless, if you follow the step-by-step instructions below, you should be able to improve your chances of successfully fending off most malicious attacks.
Isolate your website on its own server
When you’re starting a new project, you’ll probably opt for on of the numerous cheap shared hosting plans, especially if you’re on a tight budget. In theory, this makes a lot of sense.
Performance may seem adequate, especially during the early stages, when traffic levels aren’t that high, and you can use the cash you’ve saved to improve the site’s looks and functionality. However, from a security standpoint, you will be making serious compromises.
In a shared hosting environment, your website shares the same physical server as hundreds of other projects. All domains point to the same IP address, and the files and databases of the projects hosted on the server are stored in separate directories.
The hardware resources are available on a first-come, first-served basis, meaning that if someone puts too much load on the server, every other project suffers as well. This is often referred to as “the bad neighbor effect,” and it’s especially noticeable if someone launches a DDoS attack against one of the accounts hosted on your server. If the volume of traffic is large enough, it could knock the entire machine offline, taking hundreds of websites with it.
Email deliverability will also suffer if a neighboring account sends spam and blacklists the shared IP.
All in all, there are many reasons why it’s better to host your website on its own server. In the past, this meant getting your dedicated server and, often, hiring a professional system administrator to ensure everything works fine. Nowadays, things are a bit different.
Thanks to virtualization technology, hosts can split a large physical server into multiple virtual ones. In essence, with a virtual private server (or VPS), you still have a standalone machine reserved especially for your website. You have your own IP address and hardware resources that are available to you all the time. In addition to the improved performance, this gives you better security.
Meanwhile, because they can utilize the hardware more efficiently, many hosting companies offer virtual servers at a fraction of the price of an expensive dedicated machine. You don’t necessarily need advanced technical skills to run the VPS, either.
If you get a managed virtual private server, your host’s technicians will deploy the machine and configure it for the best possible performance and security. Things like load and health monitoring, patch management, and software updates are their responsibility.
In other words, it will be the professionals who will be keeping your VPS in good working order. What you need to do is make sure you don’t render their efforts useless. And this brings us to the next section.
Use strong passwords
If getting a secure hosting account is the equivalent of installing a state-of-the-art burglar alarm system, then using simple passwords is the equivalent of forgetting to turn it on. Unfortunately, countless research papers show how badly people fail to understand this. Let’s have a look at some stats.
- According to research, over 23 million users worldwide use “123456” as their password.
- 59% of Americans use a person’s name or a birthday as their password.
- 50% of all users admit to reusing the same password for all their accounts.
If you’re a part of the figures above, the chances of having your site compromised are significant. Modern brute-force attacks are pretty advanced, so often, it’s not enough to just limit login attempts after a few incorrect guesses. Hackers employ clever techniques and tools, and weak passwords are easy prey.
But what exactly constitutes a weak password?
Digit-only passwords can be cracked in milliseconds, regardless of how many birthdays you try to fit inside them. Keyboard strings like “qwerty” and “zxcvb” are even easier to guess, so make sure you steer clear of them, as well. Dictionary words, in general, are best avoided, though there is one caveat.
It’s proven that if you stick together four common words with no logical connection between them (e.g., headphoneswatchcoachskyscraper), you’ll get a passphrase that is easy to remember but has high entropy (the metric that measures a password’s strength). The strategy is good enough to secure accounts in the modern world, but unfortunately, it’s not the most practical approach. During signup, you are usually asked to create a password with capital letters, numbers, and special characters. Trying to implement them will make things much more complicated.
Moreover, while one four-word passphrase is easy enough to remember, memorizing dozens of different ones for all your accounts is downright impossible. And it should be clear by now that you must use unique passwords for all the services you sign up for.
What’s the solution, then?
Password managers can come in the shape of standalone applications or as a part of your browser (e.g., as a Google Chrome extension). They all let you sync your data across devices and operating systems, so you no longer have an excuse for ignoring them.
Even the ones embedded in browsers now come with password-generation facilities to create properly random passwords on the go. Then, they’ll store that login data securely and autofill it whenever needed.
If you want to keep your website secure, consider using these solutions to generate and manage complex, unique passwords for your site’s backend and the rest of the systems that control it.
Secure your site’s configuration files and backend
Your site’s backend is one of the hackers’ first targets. There are several things you can do to make it more secure. Let’s have a look at them in more detail.
Change the default login URL
Out of the box, WordPress users log in to the backend via a default admin URL that looks like this: https://domain.com/wp-admin/. Joomla users use https://domain.com/administrator/, and with Drupal, it’s https://domain.com/admin/.
Changing the default settings is unlikely to fend off all attacks, but it will make hackers’ lives a bit more complicated, and that’s always a good thing.
Doing it manually requires some coding skills and could be risky, especially if you’re inexperienced. If you use a CMS, plugins and extensions can do the technical work for you. These add-ons make significant changes to your site, so before you install and activate them, make sure you have a working backup.
If you have a custom site, speak with the developer and try to come up with a difficult-to-guess backend URL.
Enable two-factor authentication
Two-factor authentication (or 2FA) is a security mechanism that requires a token in addition to the username and password during the login process. The token usually comes in the form of a code generated by an app or sent via SMS, but it can also be a hardware device that you plug into your computer.
This eliminates one of the key vulnerabilities of the traditional password – the fact that it can be stolen. If you enable 2FA on your site’s backend, you’ll add an extra layer of security that will protect you in case your credentials are compromised.
If you use an open-source CMS, enabling two-factor authentication on the site’s dashboard should be relatively easy. For example, a 2FA module is now a part of the Joomla core, and although WordPress doesn’t support it out of the box, plugins can enable it for you in a matter of a few clicks.
If you have a custom site, you’ll need to set up the functionality yourself (or have your developer do it). There are tons of open-source libraries that can do most of the heavy lifting for you, and 2FA apps like Google Authenticator also have APIs that help you pair the service to your project.
If your site’s visitors can create accounts, consider enabling a 2FA option for them as well. Not everyone will use it, but security-conscious users will hold you in higher regard because you’re thinking of them.
Restrict access to your site’s backend to a few selected IP addresses
This measure may not be especially practical if you travel a lot, but considering it when applicable is not a bad idea.
With a few lines added to your .htaccess file, you can make sure that you can get access to your website’s backend from your office and/or home networks while preventing anyone else from even seeing the login page.
First, navigate to your site’s backend directory (for example, if you use WordPress, the default one is /public_html/wp-admin/, for Joomla, it’s /public_html/administrator/, etc.) and locate the .htaccess file. You can access the account via your control panel’s file manager or through an FTP client. Those of you familiar with the command-line interface can also use SSH.
If the .htaccess file doesn’t exist, you can create it with any standard text editor. Make sure you don’t add a file extension (it’s .htaccess, not .htaccess.txt). Inside the .htaccess, you need to add the following lines:
<Limit GET POST PUT>
order deny,allow
deny from all
allow from [your IP address]
</Limit>
After you save the file in your site’s backend directory, the dashboard will only be accessible from your IP address. If you’d like to allow more addresses, you can add more allow from lines followed by the appropriate IPs.
Protect your site’s main configuration file
Most web applications have a main configuration file containing important settings and information like the database login details. In the case of WordPress, it’s called wp-config.php, on a Joomla site, it’s configuration.php, etc.
You want to ensure outside people can’t view or abuse the information stored in it. One way to do it is by setting the correct file permissions, but to be on the safe side, you can also restrict access to it via the .htaccess file in your site’s document root directory.
Here’s what you need to add to secure your wp-config.php file.
<files wp-config.php>
order allow,deny
deny from all
</files>
Disable PHP execution in specific folders
Many website builders allow users to upload their own files. In most cases, the uploads consist primarily of media files, and they are stored in a folder on your hosting account (for example, WordPress puts them in /wp-content/uploads/). However, hackers sometimes use the file upload feature to put malicious scripts on the target account and trick the web application into executing them.
These scripts can install a fully-fledged backdoor, allowing attackers to take over the entire site. One way to stop them is by disabling PHP execution in the uploads directory. To do it, navigate to the folder, open the .htaccess file, and add the following:
<Files *.php>
deny from all
</Files>
Employ a Web Application Firewall (WAF)
A web application firewall is a security system situated between the web application powering your website and the internet. It monitors and filters HTTP traffic between your site and its visitors and stops a broad range of threats, including SQL injections, XSS scripting, cross-site forgery, etc. It’s not a one-size-fits-all solution, but a good web application can shield you from quite a few attack vectors.
There’s another benefit – a web application firewall’s functionality revolves around policies, which can be changed on the fly by you or your site’s administrator. This is especially handy if you need to react to a security emergency.
For example, if you’re targeted by a DDoS campaign, a slight change in the WAF’s policies can quickly stabilize the site and mitigate the danger.
Some web application firewalls can be activated as a part of a CMS plugin. They sometimes rely on outside infrastructure, which makes them a bit slower, though this is compensated to some extent by the fact that they don’t take up any hardware resources. In other cases, a web application firewall is a standalone hardware device – a powerful but expensive solution.
If you are a ScalaHosting client, you won’t need to worry about money or resource consumption. Every hosting package bought from us, including our affordable shared solutions, is protected by SShield – a proprietary security system we’ve built in-house. It uses an advanced algorithm to monitor the traffic coming to and from your website and stop 99.8% of known malware infections.
Whenever an attack is detected, the site owner is immediately notified, so that appropriate measures can be taken. SShield is turned on by default and is not a premium feature.
Keep everything updated
The developers of your website’s software play a critical role in keeping you safe. They adapt their CMS solutions, plugins, themes, and other applications to the ever-evolving threat landscape and patch security vulnerabilities all the time.
Thanks to these patches, the CMS solutions and add-ons that power our websites can meet modern security standards. However, this will only happen if you install all core and plugin updates as soon as they come out.
Failing to keep your website up-to-date will leave enormous security holes, putting the entire project and all your visitors at risk. Hackers have advanced website scanners that can identify vulnerabilities in seconds, and the existence of off-the-shelf exploits makes their lives a whole lot easier.
Keeping web applications and add-ons up-to-date shouldn’t be too difficult and time-consuming. For example, if you use WordPress, the Update section of the WP dashboard is accessible via the main menu.
The page shows you all available updates for the CMS core and the plugins, and applying them takes a couple of clicks.
If you use Joomla, alerts about new versions are available in the Notifications section on the administrator dashboard’s homepage, and you can apply the updates in seconds.
Some CMS solutions even have automatic updates built into the core or available via a plugin. It can save you a couple of clicks and ensure that patches arrive more quickly. However, it pays to use it with caution, especially if you use many plugins and themes.
However, new versions of the web application can sometimes cause conflicts. This concerns the CMS core, the installed plugins, themes, and other products. The more add-ons you have, the greater the chance of something going wrong.
That’s why if you run a complex website with lots of traffic and plugins, it’s a good idea to test every update in a staging environment before applying it to your production site.
Remove any unused plugins and themes
Most plugins and themes contain a few media files and lots of code. As the old saying goes, where there is code, there are bugs, and sometimes, these bugs could be a serious cause for concern in terms of security. This doesn’t mean you should not use any add-ons.
Without themes, plugins, and extensions, the CMS solutions we know and love so much wouldn’t be versatile enough to cater to such a wide variety of projects.
Some will be instrumental in achieving your goals, but others will be less useful. To keep security at the highest level, make sure only the former are installed on your website.
Unused plugins can have a range of negative effects on your site. For one, they take up disk space and server resources, so they could affect your hosting fees and website performance.
An excessive number of plugins also increases the chances of conflicts, especially during updates and major changes to the CMS core. As mentioned in the previous section, new features can sometimes clash with legacy code, leading to stability issues, broken functionality, or even downtime.
However, the biggest issue is security. You can’t eliminate the risk of security breaches completely. However, minimizing the number of unused plugins on your website reduces the attack surface and makes it harder for hackers to break in.
Ideally, you’ll put the add-ons you install through a careful vetting process. Read the documentation and check out the reviews to understand what benefits they can bring to your site. If you think they may be worth a try, test them in a staging environment first and only install them on the production site if you’re happy with the results.
Last but not least, don’t forget to review the list of installed extensions every now and again to make sure you have removed the ones you don’t need.
Set the right permissions
Improper file and folder permissions can mess up your security efforts. They are the primary server-side access level control mechanism in Linux, and for people who have no experience with the open-source operating system, they can be a bit confusing. Let’s try and explain them.
There are three permission types:
- Read – Read permissions allow users to view the contents of a file or folder.
- Write – With Write permissions, the user can modify the contents of a file or a directory.
- Execute – The Execute permissions allow users to run programs in the specified directory.
The permissions above can apply to three groups of users:
- Owner – Owner permissions apply only to the file or directory’s owner.
- Group – The Group permissions concern the group assigned to the file or directory.
- All users – The All users permissions refer to users that don’t belong to the groups above the system.
Linux’s command-line interface displays permissions using the r, w, and x letters. As you may have guessed already, “r” is for read, “w” is for write, and “x” is for execute.
The owner permissions are displayed first, followed by the group permissions, and the ones for all users. A “d” indicates a directory, and if a particular permission type is not given, it’s replaced by a “–“.
To view file and folder permissions, you need to use the ls command followed by the -l attribute.
Here’s what you’ll likely see if you use it in a folder with WordPress installed in it.
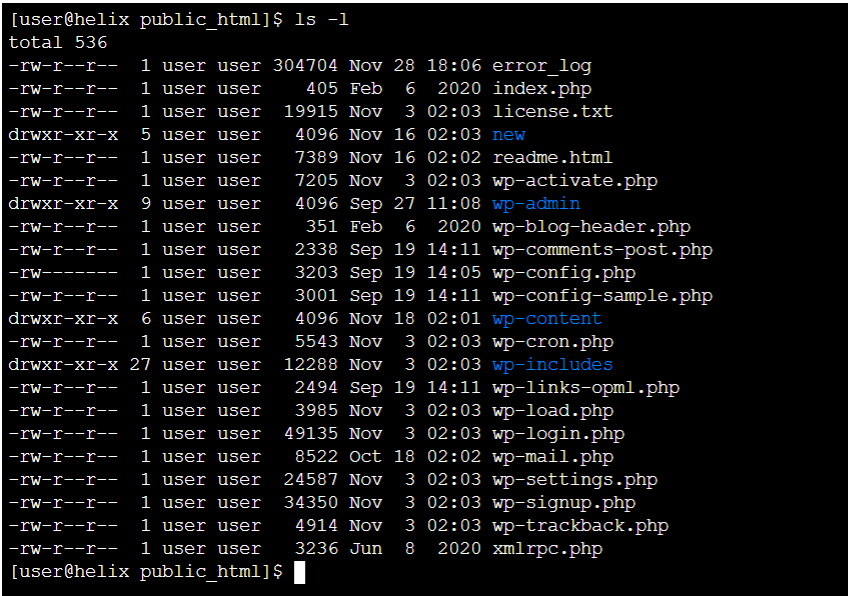
The output above tells us, for instance, that the file wp-cron.php has read and write permissions for the owner and read permissions for groups and all users. It also shows that the wp-content directory has read, write, and execute permissions for the owner and read and execute permissions for the groups and all users.
If you use a graphical user interface to manage your files (e.g., your control panel’s File Manager or an FTP client), you’re more likely to see permissions indicated with the help of a string of three digits between 0 and 7. Here’s what the digits mean.
- 0 – No permission.
- 1 – Execute permission.
- 2 – Write permission.
- 3 – Write and execute permissions.
- 4 – Read permission.
- 5 – Read and execute permissions.
- 6 – Read and write permissions.
- 7 – Read, write, and execute permissions.
Once again, the first digit concerns the file’s owner, the second indicates the group permissions, and the third – the ones for all users.
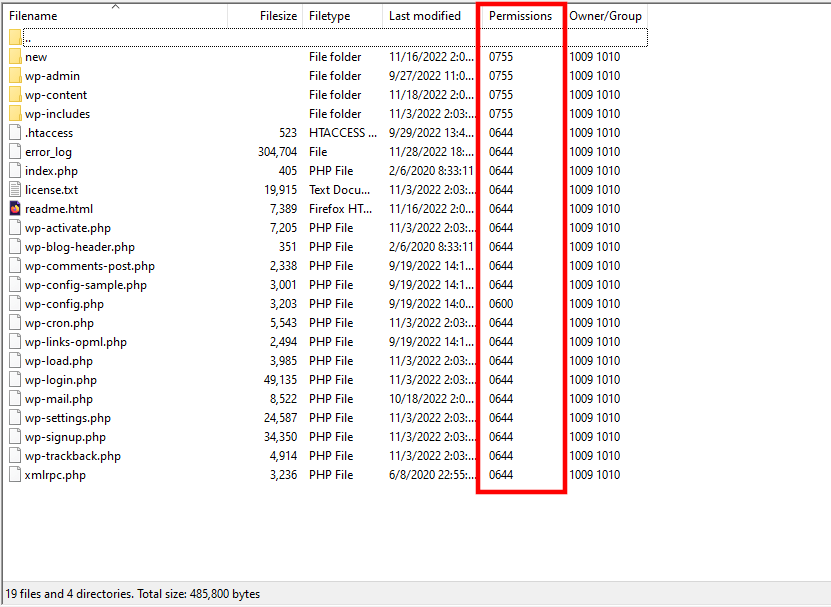
The numeric display is easier to understand, so that’s what people usually use when they need to change a file or directory permission.
If you use a file manager or an FTP client, you need to click on the item you want to modify and select Permissions. Usually, you can enter the digits indicating the permissions for each group or set them via checkboxes.
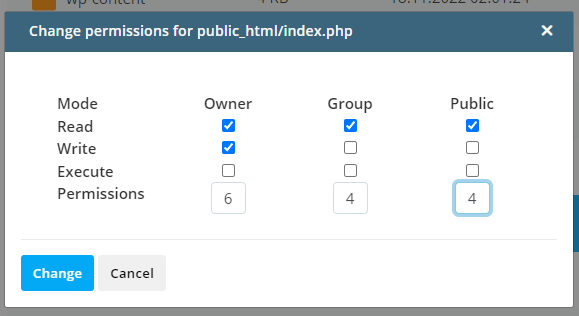
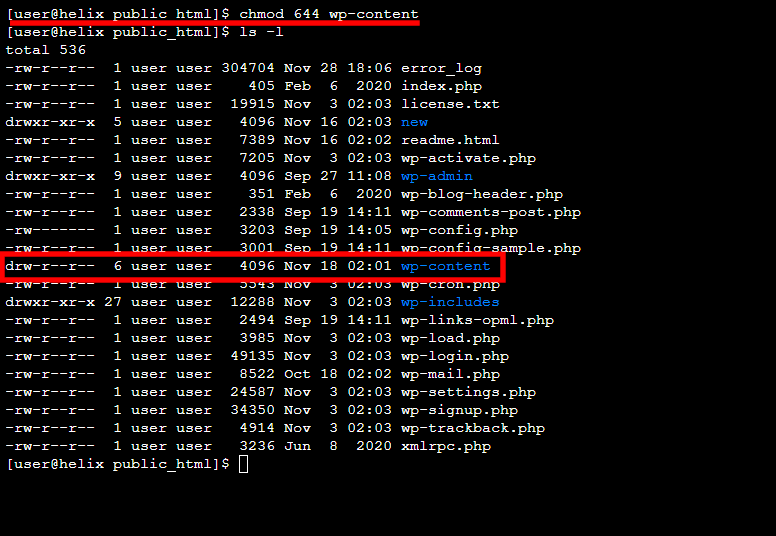
You can do it through SSH, as well. You need to use the chmod command, followed by a numeric representation of the permissions you want to set and the name of the file or folder you’d like to modify.
For example, if you want to set 644 permissions to the folder wp-content, you need the following command:
$ chmod 644 wp-content
Using ls -l, you can confirm that you have successfully changed the permissions.
Although there are exceptions like the wp-config.php file in WordPress, it’s generally accepted that permissions for individual files should be set at 644 while the ones for folders should be at 755.
Enable HTTPS encryption
Every time a user interacts with your website, their browser sends HTTP requests. Often, these requests tell the website server what sort of data the user is trying to access. However, sometimes, they also contain sensitive information. For example, when you’re trying to log in to your account, your credentials will be wrapped in an HTTP request so the server can check them.
After they are validated, the server responds with the data inside your account, which usually contains, among other things, your personal details.
In both cases, you don’t want anyone having access to or tampering with the information being exchanged. An encrypted connection is the best way to avoid this. It’s signified by the lock in your browser’s address bar, and if you want to have it, you need to install an SSL certificate.
It uses the Transport Layer Security protocol and a complex key exchange mechanism, to encrypt the data exchanged between users and the server and ensure nobody can access or modify it.
In the past, SSL certificates used to be expensive and required a dedicated IP, meaning they were reserved primarily for large ecommerce stores handling credit card data and other sensitive information.
Over the years, however, man-in-the-middle attacks evolved, and hackers started setting their sights on smaller projects for eavesdropping, injecting malicious scripts, and redirecting users to phishing pages.
Internet companies responded by setting up Let’s Encrypt – a non-profit certificate authority that issues SSL certificates free of charge. SSL certificates no longer require a dedicated IP, so every website owner can now secure their project.
Manually installing an SSL certificate is tricky, but you often don’t need to do it yourself. For example, if your domain resolves correctly, SPanel, ScalaHosting’s proprietary VPS management platform, will automatically set up a Let’s Encrypt certificate as soon as the server is deployed.
Even if the domain is not configured to work with the new VPS, SPanel can automatically install a new certificate if you point it within 24 hours of signing up. After that, you can set it up via the SSL certificates tool in SPanel’s User Interface.
Even with an SSL certificate installed, however, some web applications may attempt to load content through an insecure HTTP connection. To stop this, you need to implement HSTS.
HSTS stands for HTTP Strict Transport Security – a security policy introduced by Google in 2016 that forces the server to only serve content over the secure protocol.
Instead of redirecting requests for HTTP content to the HTTPS URL, the HSTS policy will force the server to go straight to the secure version of your site and will therefore eliminate the risk of someone tampering with the data.
To enable HSTS, add the following to the .htaccess file in your website’s root directory:
Header always set Strict-Transport-Security “max-age=31536000; includeSubDomains; preload” env=HTTPS
Perform daily backups
Regular backups must be an integral part of your security protocols. On the one hand, they minimize the volume of lost data in case of a security incident or a glitch. On the other, they help restore your site quickly and reduce downtime-related financial damage.
Ideally, you’ll never have to use your backups, but you must make sure they’re fit for purpose should they’re ever needed. The answers to the following questions will help you ensure this is the case:
- How often should I back up my data?
The period between individual backups should be determined by the nature of your website. If the content is mostly static, you can extend it. If data is generated all the time, more frequent backups are the only way to minimize the damage in the worst-case scenario. Although the advice is not universally applicable, experts say that most websites should be backed up at least once every 24 hours. For projects with greater importance, the interval should be smaller.
- How long do I keep my backups for?
This is another important part of your security protocols. And once again, the answer depends on your project’s specifics. For many, keeping a single backup and overwriting it once every 24 hours should work fine. Meanwhile, others may prefer multiple options from the last few days. Think about your needs and look for a host or a backup solution that can satisfy them.
- Where do I store my backups?
This aspect is ignored by far too many people. Yet, you could argue it’s the most important thing. Imagine there’s a hardware failure on your host server, and you need to quickly restore your website on another machine. You have deployed a backup solution that saves a copy of your files and databases once a day, so you’re not overly worried. However, you soon realize that your backups are stored on the same server as your website. In other words, they’re as good as gone.
What are the alternatives, then?
Storing your backups on your personal device is an option, but many experts advise against it. Ideally, they will be uploaded to a remote data center that is completely independent from the one hosting your website. That way, they can be retrieved whenever they’re needed, and they’re not affected by any damage caused to your main hosting infrastructure.
- How do I restore data from a backup?
Many backup solutions create copies of your site’s files and databases and put them in an archive. To restore your site, you unzip the archive. The restore takes a while if you have a big website, and it’s not the most practical solution if you only want to rebuild specific parts.
That’s why it’s a good idea to look for a solution that gives you a few additional options. For example, with ScalaHosting’s SPanel, you can browse through the backed-up files and databases and only restore the ones you want.
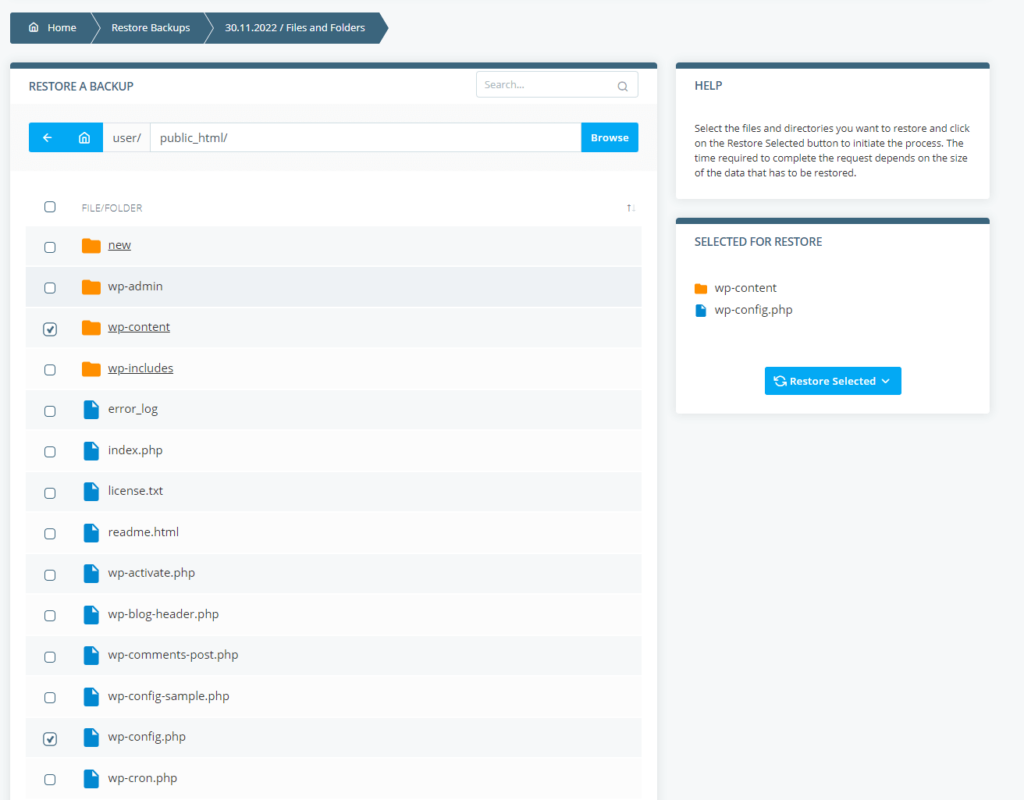
You get daily backups as standard, but three- and seven-day backup options are also available.
Last but not least, you can be sure that no matter what happens to your primary server, you can retrieve your backups because they are stored in a remote data center.
Furthermore, SPanel gives you a tool for manually backing up your entire user account, including all file types, databases, emails, and settings.
Be careful with your emails
To protect your website, you first need to protect yourself. This means avoiding phishing and other scams, which can be trickier than it seems.
First, start by protecting your own email account. Anyone with access to your inbox can reset the login data to pretty much any service they want.
Secure your inbox with a strong password and employ all available security mechanisms, like two-factor authentication.
With that ticked off, it’s time to start paying more attention to incoming emails.
As a website owner, you have a target painted on your back, especially if your site processes sensitive personal and payment information. The more popular the website, the more likely you are to fall into the scammers’ sights.
They’ll likely craft their emails to make them look like they’re coming from a trustworthy source. In some extreme cases, they may even be prepared to engage into an extended exchange to try and gain your trust.
That’s why it’s vital to check every email in your inbox before opening it and take everything you read with a pinch of salt.
Extra caution is required when dealing with messages asking you for urgent action. Hackers know that if you’re in a hurry, you’re likely to miss the red flags, so they’ll do everything they can to get you to act quickly and carelessly.
If they’re determined enough, attackers will use a broad range of social engineering techniques to lure you into their trap. Yet, there is only one way to stay safe – being more careful.
Here’s some great advice you can follow:
- Ensure your email provider uses a robust spam filter that can weed out most of the junk.
- Double-check the sender address of every incoming email and be a bit more suspicious of the ones you don’t recognize.
- Don’t open attachments sent by people you don’t know and be careful with the ones coming from recognized sources. It’s always a good idea to double-check the attachment’s extension, as hackers often mask executable files as documents or archives (e.g., document.docx.exe).
- An Office document asking you to enable macros instructions should set off alarms. Although it’s been around for ages, this continues to be one of the most common malware infection vectors.
- Double-check every link the email is asking you to click. If you want to follow a link, hover your mouse cursor over it (or tap and hold if you’re on a mobile device) to inspect the URL and ensure it’s legitimate. Be on the lookout for domains that look similar to actual services (e.g., pay-pal.com instead of paypal.com).
Install security plugins
If you use open-source content management systems like WordPress or Joomla, you can consider one of the many security plugins and add-ons available on the market.
The range of features they offer is too extensive to fit in a single article, but add-ons can help you with quite a few security measures we’ve already outlined.
Here’s some of the functionality they offer:
- Active monitoring tools that keep an eye on your site for any suspicious activity.
- File scanners that periodically check for malicious code.
- Web application firewall functionality that uses policies and blocklists to control access.
- Brute-force prevention.
- A notification system that alerts you whenever someone tries to compromise your website.
You can find both open-source and proprietary options. Some add-ons have a free version and a premium one with extended functionality. Before making your final choice, you need to consider how the security plugin will affect your budget.
Read carefully through the descriptions of all available extensions and see what they offer. The add-on you choose must give you extra value and do things you can’t do manually. Otherwise, it would just take up some space and hardware resources.
Check the number of active installations, and avoid using add-ons that haven’t been tried and tested in the real world. Read through some reviews to see if the plugins you’re considering have helped others.
Run regular security audits
It’s all about staying one step ahead of the hackers. They won’t stop trying to compromise your site, so you must ensure you’ve taken the necessary precautions to render their attacks useless. This is where regular security audits come in.
A security audit can be divided into two stages. During the first one, you scan the website and the infrastructure powering it for potential vulnerabilities. The scan should be extensive and must cover every component involved in keeping your website online, including the core files and databases, the plugins, themes, and extensions, the SSL certificate, additional widgets and services, and the server’s configuration.
The vulnerability scan gives you a thorough risk assessment of the dangers your website may be facing. During the next stage, you’ll see the practical realization of these risks.
After you complete the vulnerability scan and review the results, you can move on to the penetration testing phase of the audit. During it, you simulate real-world attacks against your website and see how easy it is to compromise.
In addition to getting a practical demonstration of what hackers do to steal private information, you can also see and assess the potential consequences of a successful breach.
You can choose from a range of online tools that can help you run a security audit. Online vulnerability scanners automatically crawl your site and single out potential security holes. Some can even be used for free, though in most cases, the scanner’s full functionality is unlocked by a premium plan.
When it comes to penetration testing, the choice of tools is even broader. Cybersecurity specialists use a range of different applications to exploit your website’s vulnerabilities. Some target specific security bugs, while others are more versatile and can compromise several elements and systems simultaneously.
Running a full security audit may be daunting for less experienced users. The automated tools certainly help, but if you haven’t done this sort of thing before, you may need to take your time and research the subject a bit if you are to make sense of everything you see.
Extra caution is required when you get to the penetration testing phase, and it’s best to use a staging environment to avoid breaking anything on the live website.
Run regular malware scans
Hackers will go to great lengths to install malware on your website. Even if you’ve patched all vulnerabilities, they can use the so-called supply-chain attack to compromise one of the third-party products you use to infect unsuspecting visitors.
If they are successful, it’s vital to learn about the threat and act upon it before they do too much damage. That’s why regular scans with anti-malware software are so important.
On the one hand, they protect your users, and on the other, they help you clean the website before Google’s Safe Browsing service flags it as suspicious. Once again, you have a range of free and paid online malware scanners, all offering various tools and features.
Do some research and see which one is suitable for you. In addition to this, ask your host whether they have any extra security mechanisms that can alert you in case something goes wrong.
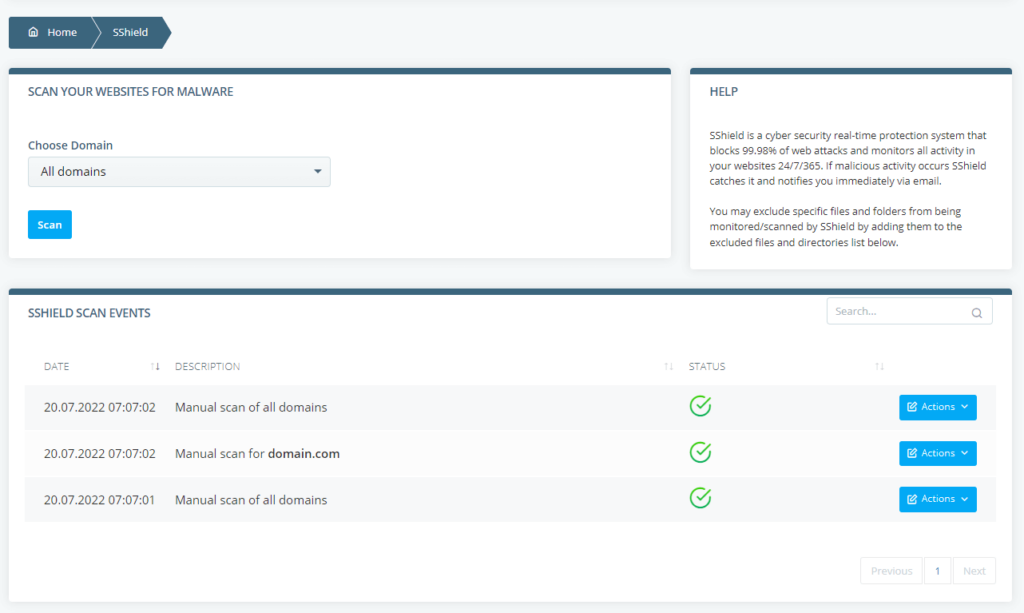
For example, if you use ScalaHosting, your account is protected by SShield – an in-house built security system tailored specifically to our services. In addition to real-time monitoring, you have a manual scan available on your SPanel VPS.
To use it, log in to SPanel’s User Interface and click SShield. You can choose which domains you’d like to check and review logs from previous scans. Excluding specific files and folders from the scan is also possible.
Use a CDN
Putting your website behind a content delivery network is one of the most efficient ways of improving loading speeds. Distributing copies of your site’s static content on a worldwide network of servers guarantees that most of the data won’t need to travel far before it reaches its destination. In addition to reducing loading times, this also lowers the load on your main hosting server, so it can handle more traffic without needing an upgrade.
However, there’s another benefit to this cloud service that isn’t discussed quite as often – the improved protection against DDoS attacks. Because your site’s files are hosted by multiple nodes, the CDN effectively acts as a load balancer, so when a large volume of malicious traffic hits it, only a small portion reaches your main hosting server. Because its IP remains hidden behind the CDN, hackers can’t target it directly, either.
Some CDN providers offer additional security features. For example, if Cloudflare users suspect their sites are targeted by a DDoS campaign, they can activate Under Attack mode from the Security > Settings menu in their dashboard. After they do it, the content delivery network will filter incoming traffic and block any suspicious requests.
Disable PHP Error Reporting
PHP can print every single error in your browser. This is useful when you’re trying to squash bugs or solve problems. However, the reporting feature can also give away quite a lot of information that hackers can use to identify potentially exploitable holes in your website.
If you use a CMS like WordPress, it will show them what sort of themes and plugins you’ve installed. If it’s a custom application, it may give them a pretty good insight into the site and file structure.
That’s why it’s a good idea to keep error reporting on while you’re in the development stages and turn it off as soon as you’re ready with the website.
You can disable PHP error messages through your site’s .htaccess file. Open it with your favorite text editor and add the following snippet:
<?php
error_reporting(0);
?>
Use Parameterized Queries
Of all the threats you’re facing, SQL injections may be among the most dangerous ones. They let hackers steal, modify, or delete data from your database, with the help of simple strings entered into the site’s text fields.
Parameterized queries are arguably the best way to protect your website. But how do they work, exactly?
Parameterized queries are also known as prepared statements. Every field on the web page has a pre-prepared SQL statement ready to be executed. The user’s input is attached as a parameter to the statement, and the command is sent for execution.
This way, even if the attacker tries to inject a malicious query into the field, it will be treated as a variable, not a separate command.
The methods for implementing parameterized queries vary according to the programming languages and the web application. The Open Web Application Security Project (OWASP), an online community designed to help website administrators secure their projects, has put together a cheat sheet to guide you through the process.
Set up a Content Security Policy
A Content Security Policy (CSP) is a browser security mechanism designed to mitigate the risk of many different attacks, including cross-site scripting, data injection, malware distribution, and even defacement. When enabled, your site’s HTTP responses will contain a header called Content-Security-Policy with the directives that determine the policy.
In simple terms, a CSP tells the browser where your site’s resources can be loaded from. Resources from sources that are not defined in the CSP are forbidden, meaning hackers can’t trick the web application into serving malicious content. Here are the main CSP directives:
- default-src – used for resources that aren’t defined by other CSP rules
- font-src – used for fonts
- img-src – used for images
- script-src – used for scripts
- style-src – used for CSS stylesheets
If you want to ban all outside resources, you can use ‘self’ as a trusted source on all directives. In this case, your CSP header will look like this:
Content-Security-Policy: default-src ‘self’; font-src ‘self’; img-src ‘self’; script-src ‘self’; style-src ‘self’
If you want to have your images loaded from your own subdomain (e.g., img.domain.com) and you’re using CSS stylesheets from an outside service (e.g., fonts.googleapis.com), the CSP header will look like this:
Content-Security-Policy: default-src ‘self’; font-src ‘self’; img-src img.domain.com; script-src ‘self’; style-src fonts.googleapis.com
Explore additional security features offered by your host
Some hosting providers create bespoke features and monitoring systems to help site owners protect their projects. If you’re looking for a new hosting company, it might not be a bad idea to consider these tools when making your final decision. It’s definitely worth taking advantage of them whenever you can.
For example, if you’re using an SPanel server to host WordPress websites, you can improve your security with our proprietary SWordPress Manager. In addition to helping you install the WordPress core software with a few clicks, it offers a couple of features that can keep it safer.
Using the Auto-Update feature, you can ensure that all security patches will be applied as soon as they are released. It covers both the core and all installed WordPress plugins and themes, so nothing will be missed.
In addition to it, you also have the Security Lock feature. With it, you effectively lock your website’s files and folders and prevent hackers from modifying them.
SWordPress also lets you clone installations in other folders on your account. You can use these clones as a staging environment where you can test all the changes to your site before implementing them into production.
Conclusion
Website security is a scorching hot topic nowadays, and we hope this article helped you realize why this is the case. Most website owners face an increasing number of threats, and many struggle to understand what they need to do to protect themselves.
The truth is, securing a website is a lot more complicated than ticking off a few tasks. Although we covered most scenarios, even the list you see above may not be extensive enough to guarantee complete protection.
What it should do, however, is show you that if you want to properly secure your website, you need close attention to the finest detail and a no-stone-unturned attitude.
FAQ
Q: How to find out if my website is secure enough?
A: You can start by assessing the risk and figuring out what the most probable threats are. This will give you a list of potential weak points which you can inspect and secure.
Q: How much does your website’s security cost?
A: The price for a really secure website can greatly vary. Smaller web projects that are built on a CMS can find suitable add-ons for the task, and it’s not a rarity to get them for free or at a minimal cost.
Custom-built and enterprise projects rely on a much more complex infrastructure, and their needs can often exceed the standard market offerings. Companies often hire outside cybersecurity agencies that can charge hundreds, even thousands per month.
Q: Can you get hacked just by visiting a website?
A: It is entirely possible to get your personal computer or smartphone compromised just by visiting an infected site. Luckily, popular browsers have learned to identify highly insecure HTML pages and duly blast you with a warning before entering such websites. You will get details of the detected issue and still get the chance to continue at your own risk.