Best Practices for Securing a Drupal Website on a Hosting Platform
Drupal is rarely the first platform the regular Joe and Joanne think of when starting a new website. That’s what the figures suggest, anyway. According to W3Techs, only about 1.5% of websites whose Content Management System (CMS) is known use Drupal.
However, when you dig deeper, you’ll see an interesting trend in the usage stats. At the time of writing, BuiltWith says that of the top 1 million websites, around 2.4% are based on Drupal. If you look at the top 100 thousand sites, the figure sits at 5.4%, and in the top 10 thousand, their market share grows to 6.2%.
It seems that the more popular the website – the more likely it is to go for Drupal. Certainly, there’s no shortage of large-scale projects with lots of traffic being powered by the CMS, including the websites of Tesla, the Mayor of London, the Prime Minister of Australia, and many more.
The people running these websites wouldn’t choose a platform that isn’t secure. They’ll also ensure that the CMS they’ve picked is as well-protected as possible.
Today, we’ll show you some of the best practices for doing that.
Is Drupal Secure?

Security should be high on the priority list of any website owner, so before you choose a platform for your project, you want to ensure your pick is robust enough.
The truth is most of the applications you are likely to consider for your new project are held to a certain standard. Unless you’re trying out something brand new – the app you’ll end up using has probably proven itself to be a suitable platform for a typical website. This is undoubtedly the case with Drupal.
It first appeared in 2001, making it older than its key competitors. Over the last two decades, the people running the project have had enough time to establish and enforce rules and policies to keep the Drupal ecosystem secure and reliable.
Drupal is fully open-source
Drupal was conceived as an open-source project from the very beginning, and it remains faithful to the same principles to this day. This means everyone can open the CMS’s source code, review it, tweak it, and redistribute it.
On the one hand, this means that the app is free to use. Anyone can download Drupal from the official website and install it on their web hosting account without paying a penny.
On the other hand, the CMS allows experts and engineers to pour over the code and identify a potential security hole or mistake. The open-source community has no incentive to keep the vulnerability hidden, so it’s immediately reported to Drupal’s development team, who work on developing a patch and promptly releasing it to users.
Drupal has a dedicated security team
Unlike other open-source projects, Drupal has a team of engineers and developers explicitly dedicated to security. Their job is to ensure high coding standards are applied to the core and the main API and that all modules are upheld at all times. To do this, the dev team writes documentation that helps other web developers produce clean and secure code. For website owners, they have guides and tips on what can be done to keep Drupal as safe as possible.
Needless to say, part of their job is also to process vulnerability reports and coordinate the release of patches.
Best Practices for Securing a Drupal Website
The people running Drupal are doing everything they can to keep the ecosystem secure. However, this doesn’t mean you can stand back and relax. While Drupal is an excellent platform to build a secure website, it’s up to you to implement all the best security practices to protect your project.
Let’s have a look at some of them.
Regularly Update Drupal Core and Modules
Updates are the only way to ship the patches for any security vulnerabilities found in Drupal or its modules. If you install the latest update, you plug the hole, and your site is safe. If you don’t – the vulnerability is active, and you could fall victim to a cyber attack.
Because installing the latest version of the Drupal core and all its modules is so important, the development team has embedded a feature into the CMS that checks for available updates and informs the site administrator if there are any.
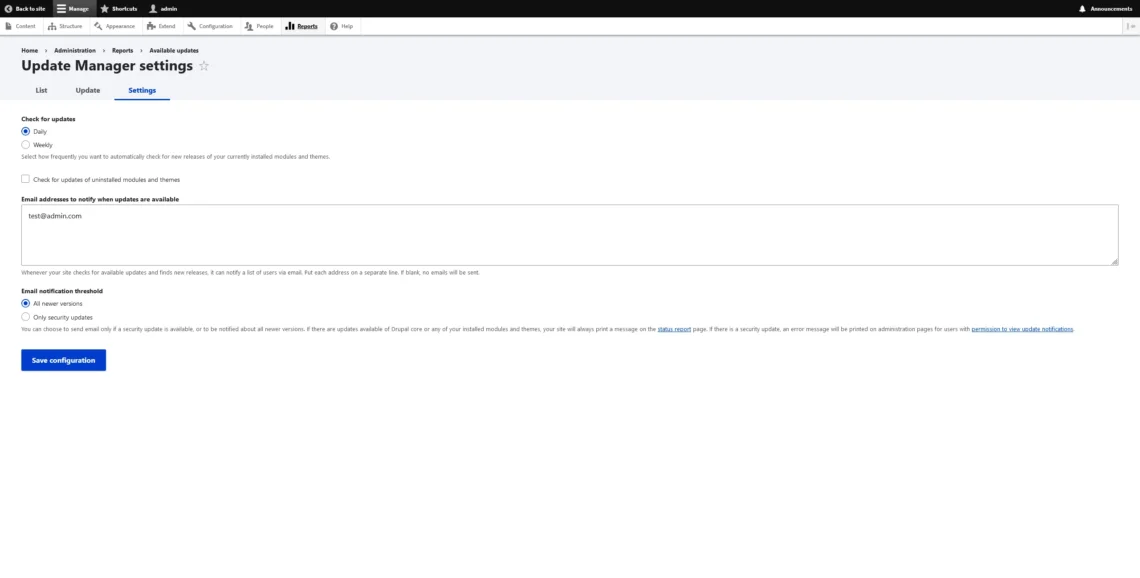
To be sure you are always up to speed, simply log in to your admin panel and go to Reports > Available Updates. Ideally, you’ll see a list on the screen that looks like this:

Via the Update tab, you can manually check for updates, and if you click Settings, you can configure how often the checks should be carried out and where the notifications should be sent.
Whenever an update is available, it will show up in this menu. However, to install it, you have to go to the Extend section and click the Update tab. Drupal has a wizard that will guide you through the process of downloading and installing the update. It’s recommended to back up the website before you begin and put it in maintenance mode while applying the updates to avoid service disruption.
Implement Strong Password Policies
Over 80% of confirmed data breaches are the direct result of weak, stolen, or reused passwords. Imagine how much safer the internet would be if people weren’t so careless with their login credentials.
So, what can you do to change all this?
Well, it starts with your own habits. If someone managed to crack your Drupal admin login credentials, they can hijack your entire site and use it for all sorts of purposes. It’s your responsibility to ensure this doesn’t happen, so think carefully when choosing your admin credentials.
Make sure your password is sufficiently long, complex, and unique. Research reveals that over 90% of all people understand the danger of password reuse, and yet 60% continue to recycle their credentials on multiple accounts. Your position as a website administrator demands a higher level of password hygiene. If you haven’t already, it’s time you realize that the only way to manage your login data securely is with a password manager.
It’s not just about the admin credentials, though. By default, users are allowed to create accounts on your Drupal website. The CMS has access control features enabling you to modify user permissions and keep track of their moves. Configure them correctly, and successful attacks against individual user accounts should no longer threaten the entire site’s integrity.
You still want to avoid such vulnerabilities in the first place, though. Compromised accounts don’t make for a pleasant user experience, so you have to ensure visitors who create accounts protect them adequately.
The best way to do it is with password restrictions. By default, you can set up an account on a Drupal website and protect it with something as simple as “123.” The interface will warn you this is a bad idea, but it won’t force you to switch to a stronger password.
With modules, however, you can set up more robust password rules and ensure people stick to them. The Password Policy add-on is a good example.
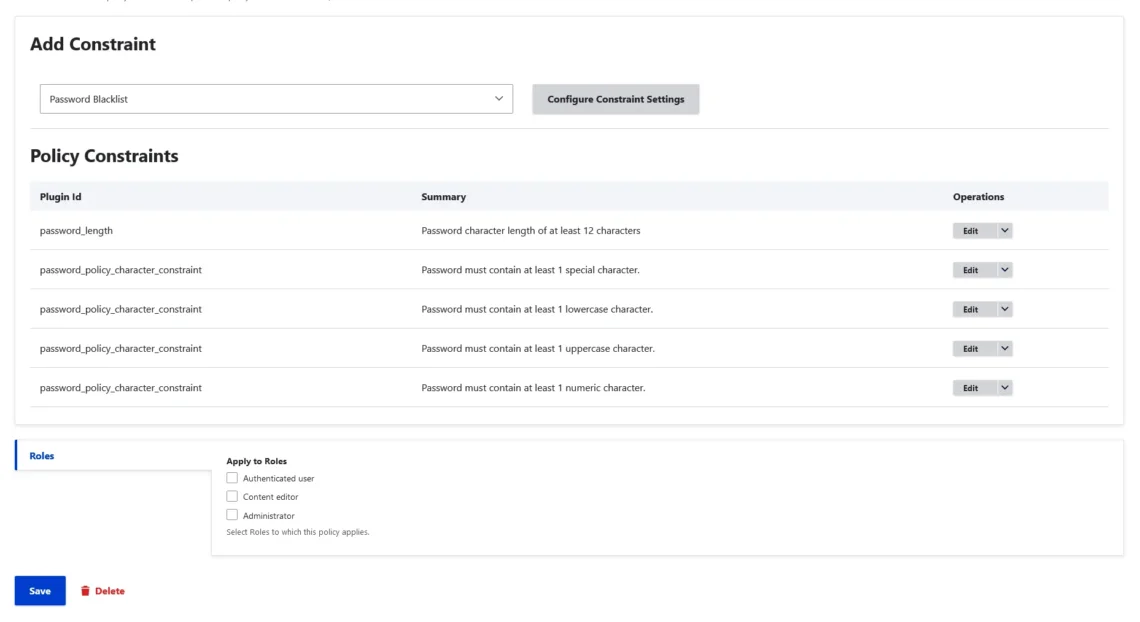
After you install it and activate its sub-modules, you’ll find a Password Policy submenu inside the Configuration section of Drupal’s admin panel. Your first job is to create a new password policy – you can set different ones for different users. You only need to choose a Policy Name and decide how often people in this group will be forced to reset their passwords.

After saving the policy, you can edit it and add the actual rules. In addition to enforcing minimum length and character type restrictions, the module allows you to create a block list of forbidden passwords, prevent reusing old passwords, or disallow passwords matching the account username.
Password Strength is an interesting add-on that builds on the Password Policy functionality. Instead of length or character requirements, it measures the entropy of every single password a user picks. You can configure it to detect and disallow common words/phrases that are considered insecure, even down to using a number instead of a letter in a dictionary word (e.g., p4ssw0rd instead of password).
Password Strength is arguably a more advanced solution, but has a couple of problems.
First, at the time of writing, its Drupal 8 version is still in beta, so you must thoroughly test it before deploying it into production. Secondly, if you’re not careful, you could make the policies too restrictive.
When deciding how tough your password restrictions should be, consider things like the volume of data stored in each account and the potential consequences if it gets breached. You want your users to stay safe but want to avoid turning the signup process into an overwhelming experience.
Securе Your Site Authentication Mechanism
Your password policies will have two distinct effects directly related to your website security. On the one hand, it will make it harder for hackers to guess people’s passwords and compromise user accounts. It won’t stop them from trying, though. Fortunately, the Drupal ecosystem has solutions that further minimize their chances of success.
For example, Flood Control is a module that effectively works as a brute-force protection mechanism. It detects multiple failed login attempts and blocks either the account subjected to the attack or the IP address initiating it. It can also prevent contact form abuse.
The offending addresses and accounts are put in a block list that you can easily manage.

The second positive effect of your password policy changes is to make users take security more seriously. Still, if they do – they’ll likely want to add another protection layer on top of their strong password. What you can offer is two-factor authentication.
Two-factor authentication (often referred to as 2FA) is an authentication system that requires something you know (your username and password) and something you have (a temporary code you receive or generate through a different device) before signing in.
Even if attackers manage to steal your password, they won’t be able to access your account as they have to guess a second code on your own device.
Drupal doesn’t support the feature out of the box, but it can be enabled with the help of the Two-Factor Authentication (TFA) module. The add-on hooks up to the Drupal login process after the user has entered their login details and the CMS has validated them.
TFA checks whether the account is protected by 2FA, and if it is – it temporarily logs the user out and redirects them to the page requiring the second authentication factor. After the correct code is provided, the user is granted access.
The TFA module gives you multiple options for the second factor. You can use an app like Google Authenticator, have the codes delivered via SMS, or integrate a third-party service like Authy.
The exact steps you need to take in order to get everything set up depend on the configuration you’re after. The first job is to create an encryption key and profile required to protect the information powering the 2FA algorithm.
The settings of the TFA module are available under the People section of the Configuration page in Drupal’s admin panel.
Secure Your Hosting Environment

The job of your hosting account extends beyond simply providing your site with the required hardware resources. It needs to give youan environment where your project operates reliably and securely. If that’s not happening, the effort you’ve put so far into protecting your Drupal site won’t amount to much.
But how tricky is it to ensure your setup is safe?
It may sound like a task that requires advanced technical skills, but the truth is, if you have the right hosting setup, you’ll do it quickly and easily. Here’s what you need to look into:
- File and directory permissions
The default permissions for files and folders are assigned automatically. Numerically expressed, they are the following out of the box:
– 644 for files, meaning the file owner can read and write a file while other users can only read it.
– 755 for folders, allowing the file owner to read, write, and execute objects inside the directory, while other users are only allowed to read and execute code without changing it.
This configuration allows a typical website to work without being exposed to any immediate threats. However, with Drupal, if an attacker manages to compromise your admin account, they can theoretically take over the entire serverif your file and directory permissions are left as-is.
Changing the permissions of specific directories inside Drupal’s core can eliminate the problem. You can do it manually, but you’ll need to do some proper research and see which directories are affected exactly.
A better option would be to use an automated add-on created just for this purpose. The tool is available in Drupal’s official repository but is not a module per se. Instead, it’s a collection of Drush (a CLI-based tool for administering Drupal) commands that do the trick for you.
Bear in mind that if something goes wrong, some of your website features may stop working. So, be sure to test the add-on in a staging environment before implementing the changes in production. It’s also a good idea to create a backup of the site.
- SSL certificate
There was a time when SSL certificates were only recommended for ecommerce projects and popular websites storing sensitive and payment information. Right now, any website, regardless of its content or size, must be protected by an HTTPS connection. There are three good reasons for this.
First, if you don’t have an SSL certificate, modern browsers will display a full-screen warning telling people they’re about to enter an unsafe website. This won’t exactly help popularize your project. On the contrary, this can only scare away your visitors and search engine robots (yes, your SEO will suffer as well).
Browsers are harsh on websites that don’t use SSL certificates because attacks are much more widespread than they used to be. For example, let’s say you use Drupal to create a personal blog where users can register accounts and comment under your posts. You don’t think it’s necessary to protect it with an SSL certificate because you don’t believe hackers could gain much if they attack your site.
However, what you fail to take into account is that during the so-called Man-in-the-Middle (MiTM) attacks, hackers can intercept the data going to and from your server and, if it’s not encrypted, use it for all sorts of nefarious purposes. They can effectively steal users’ login credentials, and because password reuse is so common, they can take over multiple accounts at other apps and services.
The third reason you should set up an SSL certificate is because there are a ton of free solutions. In the past, protecting your site with HTTPS used to cost hundreds of dollars per year and required a dedicated IP, meaning it was reserved for established online businesses only. However, the emergence of the Let’s Encrypt certificate authority means that everyone can now protect their website with an SSL certificate without paying a penny. In light of this, it makes no sense not to do it.
- Robust backup and disaster recovery strategy
It goes without saying that you must have a backup of your site. However, many take it for granted and don’t really understand what makes a good backup. There are three things you need to consider:
- Backup frequency
Your goal is to ensure that if you do need to restore your site from an archive, you lose as little data as possible. To do that, you need a fresh backup.
For most websites, a solution providing daily backups should work fine, but if your project generates data constantly, you may need a system that creates secure copies of your site more frequently. Also, some providers offer to keep older backups for more than 24 hours. Consider the options and think about whether this is something that might be useful.
- Reliability
There’s no point in having a backup that doesn’t work. Be sure you check your backups every now and then to see if they contain your full site data.
- Storage
Incorrect backup storage is far too common, unfortunately. Both users and vendors often make the mistake of placing backups on production servers or infrastructure that could be vulnerable to hardware failure.
Ideally, your backups will be stored in a different data center from your main hosting server. That way, even if there’s a serious problem with the facility or the hardware in it, you’ll have no problem recovering your website.
ScalaHosting and Drupal

Over the years, we’ve seen many ScalaHosting customers launch websites based on Drupal that ended up being really successful. We’ve also seen our fair share of flops.
This experience means we know what works and what doesn’t, and we’ve used that knowledge to build and configure our Drupal hosting plans. They were all configured with the CMS in mind and are designed to meet all your site requirements.
If you have a small project and a tight budget, you can start with one of our shared packages. For less than $10 per month, you can get a brilliant launchpad for your new site. All shared plans include the cPanel control panel and the Softaculous automatic installer.


This means you can deploy Drupal with a couple of clicks and start working on your project immediately. When it outgrows the capacity of the shared environment – you can easily upgrade to one of our VPS solutions.
With them, you’ll get a fully isolated environment, guaranteed resources, and a dedicated IP address. Our virtual servers are deployed in a robust cloud environment, ensuring blistering loading speeds and excellent uptime stats. Yet again, Softaculous is available on all accounts, and if you have an existing website, we can transfer it for you at no cost.
In terms of security, all our hosting solutions are protected by SShield – a unique security system built in-house and designed to stop pretty much all known attacks before they get the chance to do some damage.
Let’s Encrypt SSL certificates can be installed easily on all plans through tools available in cPanel and SPanel – our own server management system.
In addition, by default, every account comes with daily backups, with the option of saving them for three or seven days. All backups are stored in a different data center from the main hosting server, so they’re easily recoverable when needed.
If you want to know more about hosting services, do not hesitate to contact our sales specialists.
Conclusion
Drupal is one of the world’s leading content management systems. It may not have the market share of WordPress or Joomla, but it still flaunts a solid following. The community that maintains the project ensures it expands along with the trends, as modern websites demand frequent changes.
This community can give you all the tools you need to secure your Drupal website. You just need to know how to use them.
FAQ
Q: How do I secure my Drupal website?
A: To properly protect your Drupal website, you must consider almost every aspect of its operation. This includes installing the latest patches, improving your password management habits, implementing useful Drupal security modules, and many more. It’s not something you can finish in a day, but if you know what you’re doing – you can make a real difference to your project’s security posture.
Q: Is Drupal safe?
A: Over the years, Drupal has built a reputation for high levels of security and robust protection mechanisms. It’s open-source, so security vulnerabilities are more easily identified and addressed. Its modular architecture allows you to implement multiple additional security features, and a dedicated team ensures that the ecosystem is in good shape.
Q: How do I host Drupal on a server?
A: Drupal will run on most standard web hosting servers and stacks. It requires a database, which you’ll create through the tools provided by your host, and it comes with a handy installation wizard that can help you if you need to configure it manually. If your hosting account comes with the Softaculous automatic installer, using it is the more convenient choice.