Server Security Hardening for Drupal Hosting: Steps to Protect Against Common Vulnerabilities and Attacks
Before you start work on your new Drupal website, you have to be sure its server is correctly set up and configured to provide a secure environment.
Sounds complicated?
It probably does, especially if your website-building experience is limited. However, our job today is to show you that it’s not that tricky at all.
Once you learn more about the threats and vulnerabilities you face, you’ll quickly figure out what you and your host can do to protect your project.
Let’s take a closer look.
How Drupal Security Works?
Many people can’t visualize all the hacker techniques for compromising websites, so they’re unable to implement the right protection mechanisms to prevent a breach. Online research doesn’t always help, either.
There are far too many tutorials, articles, and other resources full of terminology, scenarios that don’t apply to your particular project, and doom-and-gloom predictions designed to strike fear into the minds of inexperienced website owners.
Instead of clearing up the picture for you, these could bring more confusion. To avoid this, try to view the matter from the attacker’s perspective.
Imagine you are a hacker who wants to breach a Drupal website. How would you approach it?
Well, the briefest of analyses reveals that there are three main targets:
- The hosting server
Every Drupal website is hosted on a physical or virtual machine, usually owned and run by the user’s hosting provider. The server is connected to the Internet 24/7, and people from all corners of the globe can connect to it. If it’s not configured correctly, an attacker could infiltrate the server and use it for all sorts of nefarious activities.
- The website
Next is the software supporting the website, namely, the Drupal core and its themes and modules. We have thousands of lines of code, each of which could contain a security bug. Depending on the severity of the vulnerability, a potential exploit could allow anything from a drop in performance or a functionality glitch to a complete site takeover.
- The people working on the website
One can argue that humans are always the weakest link in any security chain. They’re certainly highly vulnerable. If you’re the only person working on your website, a single set of login credentials grants attackers full access to Drupal’s administration panel. These credentials can be stolen, lost, or guessed, and in the wrong hands, they could wreak total havoc.
In other words, as a website owner, you have three main fronts to defend. There are a few techniques to implement and protect them.
The Basics: Password, Access Level, and Security Policies
Some of you will be managing your Drupal site on your own. Others will be a part of a team. In both cases, the challenge is guaranteeing maximum security with minimal interference in people’s everyday work. You can start with the simplest and most common security device.
Passwords
Much has been written over the years on how to create strong password policies. Some of the best practices that were relevant a while ago have fallen out of favor with experts.
For example, forced periodic password resets are now considered somewhat pointless. According to many security specialists, they inconvenience users and encourage them to use easy-to-guess variations of their old passkeys. Their overall efficacy in boosting the site’s security is also questionable.
Not everyone agrees, though.
Many websites continue to implement a password expiration policy. If you want to do it as well, a contributed Drupal module called Force Password Change enables this functionality.
However, other techniques will bring more value to the table.
- Enforce strong password restrictions
We all know that a good password contains uppercase and lowercase letters, numbers, and symbols. It’s not as simple as that, though. If it were, a password like “Password123!” would be considered reasonably robust, yet it clearly isn’t.
If you want your site to be secure, you must ensure its users, especially those with access to the administration pages, don’t use such passwords. Installing the Password Policy contributed module may not be a bad call.
However, no matter how long and random your password, it won’t be good at protecting your site if it’s been leaked on the internet. Given how many login credentials are breached and unleashed on dark web forums for free, the possibility of this being the case isn’t as remote as you may think.
That’s why, a few years ago, security expert Troy Hunt launched a service called HaveIBeenPwned. He collects vast databases of login credentials stolen from various websites and services and leaked publicly. On his website, you can check whether your email address and passwords have been breached.
Hunt has also built an API that lets you integrate the HaveIBeenPwned service into your project, and predictably, the Drupal community has done the heavy lifting for you. The only thing you need to do is install the Pwned Passwords module. This way, you can stop users from setting passwords that have already been compromised.
- Eliminate passwords whenever possible
It’s clear that although we’ve been using them for decades now, we often struggle to create passwords that can adequately protect our accounts. So, can’t we just get rid of them altogether?
More often than not, this is impossible. There are exceptions, though!
By default, you access your hosting server via SSH with the help of your hosting account’s username and password. As a server administrator, you can also grant individual website owners SSH access through their control panel login credentials. However, after you open a shell, you can use a local SSH client like PuTTY to generate an SSH key. Then, with a few quick commands, you can configure the server to use the key to authenticate your account.
Key-based authentication is considered more secure and will save you a couple of clicks whenever you need to open a new shell. The downside is that you can only use the key if it’s available on the computer you’re currently using.
If you’re sure everyone with access to the server has their own workstation with their key stored on it, you can disable password authentication altogether. You simply need to edit the primary SSH configuration file (/etc/ssh/sshd_config), which requires root access. Find the line that says:
PasswordAuthentication yes
In some cases, it may have a # sign at the beginning.
Change the line to:
PasswordAuthentication no
To apply the changes, restart the SSH service.
NOTE: Be sure to think this through carefully. If you feel there’s even a remote chance of getting locked out of your server because you’ve disabled password authentication, it’s best to leave this option turned on. Just make sure your passwords are stored properly and are difficult to brute-force.
- Use 2FA
Two-factor authentication (or 2FA) is an excellent way of adding an additional layer of security to your account. When enabled, it adds a second step to the login process, requiring you to enter a temporary code or password generated by an application on your smartphone or sent via SMS or email.
Two-factor authentication is often available at several different access points:
- Your Client Area
This is the dashboard on your host’s website where you control your active hosting services. If hackers breach it, they could access or suspend your server, disrupt your site’s operation, and steal personal information. Given this, it should be easy to see why some additional security wouldn’t go amiss.
- Your control panel
Popular control panels and server management systems like SPanel and cPanel support 2FA and enable you to keep hackers away from the tools you use to manage your server and all the projects hosted on it.
- Your Drupal website
Using a contributed module called Two-factor Authentication (TFA), you can enable the functionality on your site as well. It supports multiple 2FA methods and has a reliable fallback feature, ensuring you’ll never lose access to your site. Role-based implementation means you can choose who will use the feature.
Access Control
Proper access control on all levels is critical for your Drupal site security. There are multiple entry points, and you must be able to track who’s using them and how.
Privileges must be assigned to the people who work on your website and server on a need-to-use basis. In other words, they must be able to access only the resources they need to do their jobs.
So, how do you ensure this is the case?
- Remove SSH access for the root account
The root account in Linux is the server administrator with full privileges over the operating system and all the software applications installed on it. It can modify every file and core setting, and website owners can use it to configure a custom hosting environment for their projects.
Sadly, there’s a slight problem with that.
The root account’s username is always “root,” so if hackers want to gain access to it, all they need to do is guess the password. In other words, the most powerful account on the system is also the easiest to brute-force.
Thankfully, root SSH access can be easily disabled. Before you proceed, make sure you have at least one other account with superuser privileges, preferably with a username that is not too easy to guess. Open the main SSH configuration file (/etc/ssh/sshd_config) and look for the line that says:
PermitRootLogin yes
Change it to:
PermitRootLogin no
Restart the SSH service to apply the changes.
From now on, only accounts with superuser privileges can perform root tasks. In addition to having unique usernames (which makes them trickier to brute-force), these accounts must also use su or sudo whenever root privileges are required, making it easier to keep track of who is doing what on the server.
- Secure control panel access
When you’re not managing your site and server exclusively via SSH, you’re likely using a server management solution like SPanel or cPanel. Out of the box, these platforms come with plenty of tools that make website management easier and more secure.
After your server is deployed, your first job is to log into your control panel’s Admin Area (on cPanel servers, it’s called WHM or Web Host Manager). From there, you create a user account for your Drupal website.
If you use SPanel, you can choose which features will be available to the new account, thereby improving the server’s overall security. For example, you can disable email tools if you don’t plan to use the account for communication purposes. That way, even if someone gains unauthorized access to the user interface, they won’t be able to set up an email inbox and use it to send spam.
Feature access is fully customizable. You can activate and deactivate tools at any given time, so you have complete control over what user accounts can and can’t do.
Furthermore, both SPanel and WHM/cPanel let you modify various server resource limits, and you can decide whether the account owners will have shell access.
Once the user account is deployed, its owner can add sub-users and delegate specific tasks to them. For example, if you have a database administrator, you can assign a set of login credentials and access to the database-specific tools only.
You can also grant others access to your server management platform’s admin interface. Yet again, deciding what privileges they’ll get is up to you.
Overall, both SPanel and WHM/cPanel provide granular access control, which is critical for ensuring the safety of your server.
- Secure Drupal Access
Let’s say you have a Drupal website with a few landing pages and a blog section. A content writer produces articles for the blog, and because you’re building an international business, you have hired a few translators to adapt the site to other languages.
These people need access to the Drupal back end. However, if you grant them full administrative privileges, you risk someone, willingly or not, doing something that could affect your Drupal site behavior. In other words, while your employees must be able to edit and translate content, you must ensure they don’t have access to the site’s theme, modules, core settings, etc.
Luckily, with Drupal, doing this is pretty straightforward.
You can manage registered users and their privileges through the People section in your site’s back end.
You have three tabs: List, Permissions, and Roles. We’ll start with the roles because they determine visitors’ access to your site. The three default roles in Drupal are Anonymous user, Authenticated user, and Administrator.
The anonymous user is the visitor who hasn’t created an account. By default, they can view the content you publish, use the search functionality, and read the comments other people leave under your site’s articles. An authenticated user has an account protected by a username and a password. Out of the box, the difference between an anonymous and authenticated user is whether or not they can post comments. However, as you install additional modules, you unlock other functionalities that you can enable for people with registered accounts. Authenticated users log into their accounts through the site’s front end and don’t have access to the Drupal administration panel.
The Administrator role’s name is pretty much self-explanatory. It grants the user complete control over the site’s front and back ends. All features are enabled by default and can’t be turned off.
As an administrator, you can create new roles or edit existing ones. The Roles tab under the People section of Drupal’s back end lists all currently existing roles and has a button labeled Add Role.
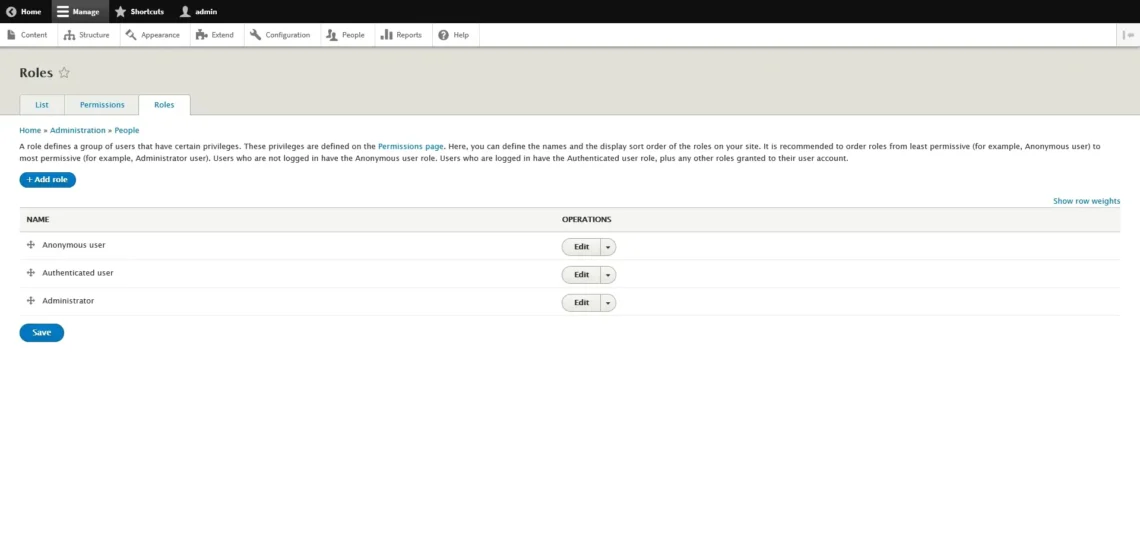
When you click it, you’ll be asked to think of a name for the new role. After you pick one and click Save, you’ll see the new role in the list. Next to each role, there’s an Edit drop-down menu, and under it, you can select Edit Permissions to determine what sort of privileges each role will give users.
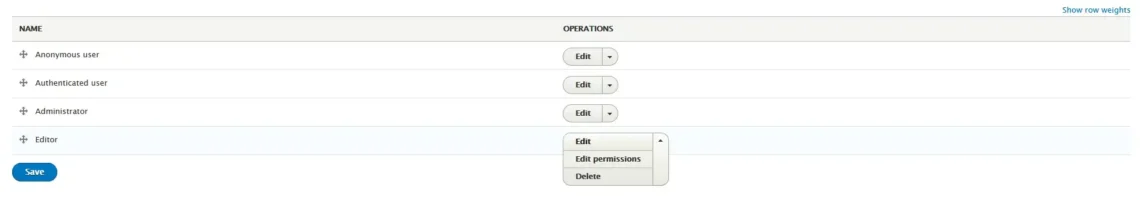
The exact list of permissions depends on your modules. However, access control is highly granular, so you always have complete control over the privileges of each group of users.
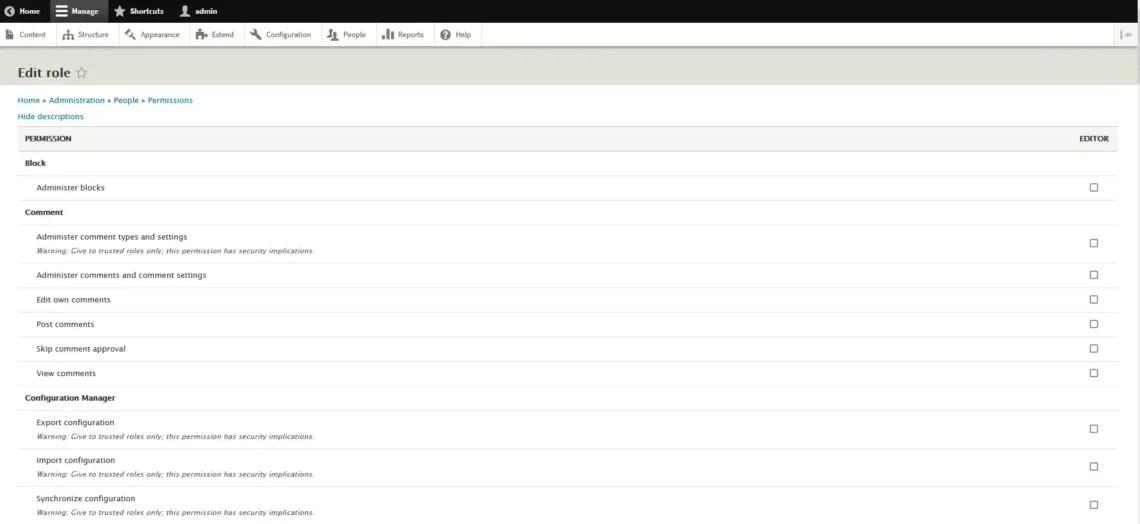
To return to our example, you’ll have to create one role for your content writer and another for the translator.
You can even determine whether users will have control over their content only or whether they can edit every article published on the Drupal website. This way, multiple contributors can create content, and a single editor-in-chief can be responsible for the quality.
When adding a new user account from the People section of Drupal’s administration panel, you can choose the role you’ll assign to it. A single user can have multiple roles, which gives you even more control over what people can and can’t do on your site.

Correctly delegating tasks is essential for optimizing the workflow and building a secure website, so explore all the options Drupal offers.
Install Updates as Soon as They’re Available
Your website is built with Drupal, but behind the scenes, you have many other solutions working to ensure the best possible hosting environment. Let’s take a look at some of the most critical ones.
- The operating system
In essence, a web hosting server is a really powerful computer. Like any computer, it needs an operating system. In the case of web hosting servers, the operating system is usually Linux.
- The web server
When visitors try to access your website, their browser sends multiple requests for the different components that make up the web page. The web server is the platform that locates the requested data and sends it back to the user.
- The database management system
Your website won’t work without a Drupal database. The software you need to ensure reliable data flow to and from it is called a database management system (DBMS), and it’s a part of any web hosting account.
- The mail server
Most providers pack their web hosting services with the ability to create inboxes associated with your domain name and use them for business communication. To do this, hosts install mail servers, which enable you to create email inboxes and send and receive messages with the rest of the world.
- The PHP interpreter
Out of the box, your server doesn’t understand PHP, the programming language Drupal is written in. It relies on a PHP interpreter, which translates the code in your site files into instructions the server understands.
- The control panel
Most hosting accounts, especially managed services, come with a server management platform and/or a control panel that automates many day-to-day tasks related to building your Drupal website or the rest of the services packaged. These solutions allow you to launch and build a successful Drupal project without advanced command-line skills.
In other words, in addition to Drupal and its modules, you have a ton of software crucial for the functionality of your website. Any bugs in that software can put your server security at risk. Unfortunately, with such a large volume of code, bugs are inevitable.
What you can do is prevent hackers from taking advantage of them.
The online world relies on security researchers who thoroughly examine all commercially available software and look for potential vulnerabilities. When they find them, they report them privately to the vendors, who work hard on implementing fixes. The patches are released with the next version of the affected application, and you need to ensure they make their way to your server as soon as possible.
Whether it’s your web server, DBMS, or control panel, all software must be fully up-to-date at all times. Here are the two main challenges to look out for:
- Keeping downtime to a minimum
Updating a software application usually requires restarting its processes, which inevitably disrupts the website. To minimize this effect, you should plan your updates carefully and schedule them for the most appropriate time of day.
- Potential bugs and conflicts
With so many critical components working simultaneously to support your Drupal site, you shouldn’t be surprised to learn that even minor changes could have serious implications. That’s why caution should be applied every time an update is installed. Ideally, you have a staging environment to test every new version before rolling it out to the live site. If you don’t, try to do your research to see if any potential compatibility issues may arise. As always, ensure you have a recent working backup before making any changes.
If you’re trying to make a hosting environment more secure, updating all server software to the latest available versions should be high on your priority list.
Configure Your Firewall Correctly
In simple terms, your firewall is the filter that determines which incoming requests hit your web server and which ones are blocked. There are many solutions on the market, all boasting a range of advanced features. Some firewalls come with extras like deep packet inspection, intrusion detection and prevention systems, traffic encryption, AI integration, etc.
However, the firewall’s efficiency depends on its deployment and configuration. In other words, it’s all in the hands of the server owner or administrator. Here are a few tips you may need to keep in mind if you’re tasked with setting up your firewall.
- Block all ports you don’t need
Make a list of all the services your Drupal website, its modules, and peripheral services (like email, SSH, etc.) use, and see which networking ports they communicate through. All unused ports must be closed. This will reduce the attack surface and make monitoring and blocking potentially malicious traffic easier.
- Introduce a deny-all by default model
Also known as a whitelist approach, this model involves deploying a firewall that blocks all incoming requests except those allowed in its configuration file. The traffic is easier to manage, and you get more control over who accesses your Drupal website, which could be a massive security benefit.
- Change the default SSH port
The SSH protocol gives you access to key server settings and files. Even without root access, a hacker could do a lot of damage through it. That’s why, besides taking all security precautions, it’s a good idea to change the default SSH port. It won’t necessarily stop every attack, but it could be enough to thwart some automated brute-force attempts.
- Limit outgoing traffic and use application-specific rules whenever possible
You can’t restrict outgoing traffic completely, but be sure it’s limited only to the necessary destinations. Use application-specific rules to determine which apps will have access to what traffic if supported.
- Monitor and log traffic
Set up a monitor and logging mechanism to track traffic and review past events for suspicious activities. Some firewall solutions can send alerts when they detect sketchy requests, which could help you react quickly to potential threats.
The firewall is the first line of defense against the numerous attacks your Drupal website will face over its lifespan, so don’t underestimate its importance.
Employ a Solid Anti-Malware Scanner
When choosing a content management system, many compare various aspects of the platforms’ operation. Some of the most common questions they ask revolve around security, and Drupal has much to offer in that aspect.
In addition to the large number of security modules, Drupal is also renowned for its built-in security. What’s more, because you’re not using the most popular CMS, you’re less likely to get attacked than WordPress users, for example.
Nevertheless, you can leave nothing to chance. A secure web hosting server must contain a reputable anti-malware solution that scans your account regularly and looks for suspicious files or processes.
ClamAV is among the most popular anti-malware applications for hosting servers. Its advantages include easy integration with popular web hosting control panels, comprehensive threat detection, email protection, excellent performance, and more.
Being free and open-source also helps.
Naturally, there are many AV scanners and applications, offering a wide range of features at different prices. Be sure to research them all before deciding which one best fits your project.
Perform Regular Security Audits
Securing a server isn’t a set-it-and-forget-it task. The online landscape changes constantly, and the threats you face evolve. This means the security precautions you take today won’t necessarily be adequate in a few months.
It’s essential to keep your finger on the pulse and educate yourself about the latest and most dangerous attacks hackers develop and launch against websites and applications.
Staying one step ahead of cybercriminals may sound like a tall order, but the truth is that the open-source community and the security industry provide the resources you need to do so. You just need to ensure you implement them in the best way possible.
ScalaHosting and Drupal Server Security
Today, we covered quite a few scenarios and potential weak points that could expose your Drupal site and web hosting server to attacks. As you build your site, you may discover some more.
That’s really not a problem with the right provider.
If you opt for a managed cloud VPS solution from ScalaHosting, we’ll be responsible not only for providing you with a web hosting server on which you can deploy your Drupal project but also for delivering a hosting environment that guarantees blistering performance and bulletproof security.
Let’s review some of the key features.
- SPanel
SPanel is a proprietary server management platform created by ScalaHosting. A quick review of some of the features and functionality will show you just how important security has been throughout its development. For example, as soon as you point your domain to your new VPS, SPanel automatically installs a free Let’s Encrypt SSL certificate, meaning the connection between your site’s visitors and your server is encrypted with practically no intervention on your site.
Cloudflare integration could help you if you find yourself on the wrong end of a DDoS attack, and with SPanel, it’s done with a couple of clicks. In addition, you get many features that help you secure anything from your emails to your domains and subdomains.
- SShield
Having been in the business for well over 15 years now, it’s safe to say that we’ve seen our fair share of security incidents. We used that experience to develop SShield – a unique security system that can stop almost any cyberattack in its tracks.
SShield has an extensive database of known malicious attacks as well as advanced detection capabilities to identify and terminate any suspicious activity before it causes any damage. Any potential risk will trigger a notification so you can promptly react.
- A pre-configured service that is ready to use out of the box
A managed service means our technical experts are responsible for deploying a fully functional, properly configured server. Your VPS comes with all its components installed and configured.
You don’t need to spend time setting up an anti-malware solution, configuring a firewall, or delving deep inside the operating system’s core settings to boost defenses. It’s all ready to go out of the box.
- Ongoing maintenance and updates
You don’t need to periodically check for updates to the critical server components on your VPS. Our technicians support every managed virtual server throughout its lifecycle, so you never need to worry about testing the security patches and thinking of how to install them with minimum disruption to your site.
- Complete control over who has SSH access
With ScalaHosting’s managed servers, you have a choice. By default, your VPS comes without root access, but if you need to install additional software or would like to change the server’s core settings, you can request full control over the server, and our technical experts will comply.
As a server administrator, you also decide which SPanel user accounts you set up can open a shell.
- Daily offsite backups
Even with all the security precautions, you should never rule out the possibility of something going wrong. You must have a plan of action in case they do. To give you the best chance of recovering quickly, efficiently, and with minimum losses, our managed VPS plans offer daily backups.
Every day, SPanel automatically saves a snapshot of your server with everything hosted on it, so even if your site is knocked offline, you still have access to its data. Crucially, your backups are stored in an offsite location, eliminating the risk of losing data even in the event of a terminal hardware problem.
These are just some of the security features we’ve included in our Drupal hosting plans. You’ll be happy to hear that they are all part of the standard package and are available at no extra charge.
If you want to learn more about our services, do not hesitate to contact our sales specialists.


Conclusion
Securing a Drupal website isn’t as easy as setting up a couple of modules and hoping all is good. There are many different aspects to consider and threats to take into account.
The good news is, you don’t need to do everything yourself. A managed Drupal hosting VPS from a reputable provider will relieve you of many responsibilities. Instead of you trying to figure out how it all works, your server will be secured by a team of experienced technicians. However, your role in the whole setup is still crucial even if that’s the case.
In addition to familiarizing yourself with and following the industry’s best practices, you must also learn more about what your host has done to protect your site and determine how to make the most of the available features.
FAQ
Q: How do I restrict access to content in Drupal?
A: The People section of Drupal’s administration panel gives you quite a few tools to manage the users on your site and their access levels. Individual accounts are assigned roles, and you can decide each role’s privileges. Some Drupal models can give you even more control over who has the right to access and edit content on your site.
Q: What type of vulnerabilities can be exploited on a Drupal site?
A: The Drupal core code, as well as all open-source modules, are regularly reviewed. Every now and again, security experts find vulnerabilities that, under specific circumstances, could allow hackers to attack affected websites. Fortunately, instead of publicly disclosing their findings, the specialists work with Drupal’s development team to build patches released with a new version of the CMS or modules. What you need to do is ensure all these updates are installed.
Q: How do you make your website visitors feel secure?
A: You can start by installing an SSL certificate. This ensures the user sees a lock in the browser’s address bar, which inevitably gives them peace of mind. Implementing the right password policies should also make visitors feel secure. The challenge is to implement them without causing excessive inconvenience for users.